Injection Prevention
Injection Prevention blocks click injection, a type of ad fraud that only occurs on Android devices. Click injection inserts fake touchpoints after an app is installed but before the app opens for the first time, stealing credit for the install.
Injection Prevention uses touchpoint timestamps and app installation timestamps collected through the Google Play Install Referrer API and Airbridge SDK to identify fraudulent touchpoints and block click injection. Therefore, it cannot block click injection when apps are installed outside the Google Play Store or when Install Referrer data is not collected for other reasons.
Injection Prevention identifies fraudulent touchpoints based on their timestamps. The typical flow and timestamps recorded during an app installation are as follows:
The user opens the Google Play Store. At this point,
referrerClickTimestampSecondsis recorded.The user clicks the “Install” button in the Play Store. At this point,
installBeginTimestampSecondsis recorded.App installation is completed on the user’s device. At this point,
systemInstallTimestampis recorded.When the user opens the app for the first time, the Airbridge SDK is activated and an Install (App) event occurs. At this point,
eventTimestampis recorded.
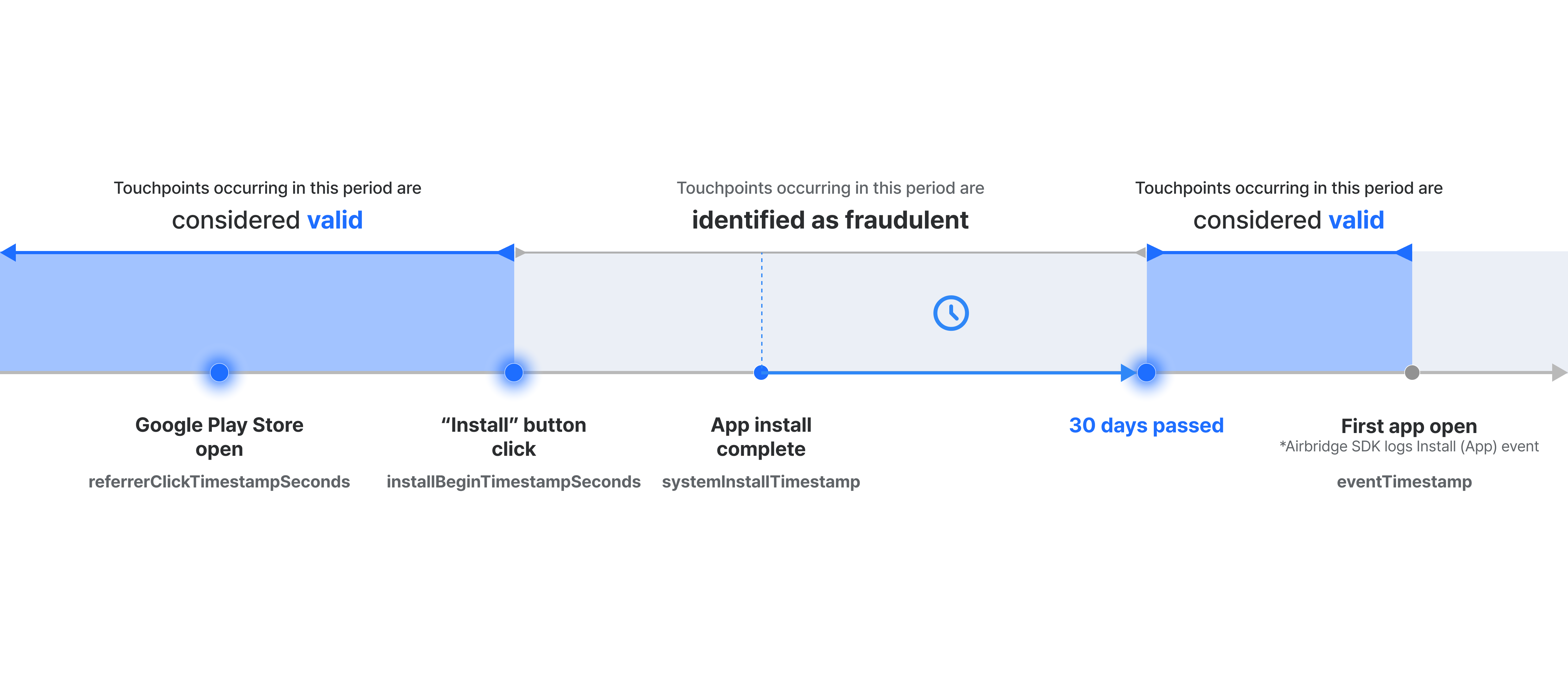
Injection Prevention considers the moment a user clicks “Install” button in the Google Play Store as the moment they decided to install the app. Therefore, touchpoints occurring before the “Install” button click are considered valid, while touchpoints occurring after the button click are identified as fraudulent.
However, touchpoints occurring more than 30 days after installation is completed are not identified as fraudulent. This is because if a user installs the app but doesn’t open it for an extended period, then opens it for the first time after a new touchpoint occurs, that touchpoint may have driven the user to open the app.
Go to [Settings]>[Fraud Validation Rules]>[Injection Prevention] to configure the default settings and the settings by channel.
Note
For Airbridge Apps registered with Airbridge before October 23, 2024, the Default Settings for both Click and Impression will be automatically enabled with the prevention level set to "Level 3."
The default settings apply to all channels that do not have customized settings. The events that are attributed to the suspicious touchpoints will be processed according to the set prevention level.
1. Switch on the toggle for click or impression, or both, depending on how you want to set the rule.
2. Select the [Prevention Level] and click Save.
Attention
It is advised to start from "Prevention Level 1" and switch to higher levels after consulting with your media partner, as the prevention level setting may have a direct impact on the ad performance.
Customized settings apply only to specific channels. The default settings don't apply to channel with customized settings. Note that the customized settings can be configured for only non-SAN channels. The events that are attributed to the suspicious touchpoints will be processed according to the set prevention levels.
1. Click Add a rule.
2. Select a channel. The customized settings can be configured for non-SAN channels only, and therefore, the SAN channels and custom channels won't appear in the search bar.
3. Switch on the toggle for click or impression, or both, depending on how you want to set the rule.
4. Select [Prevention Level] and click Save.
Events attributed to the suspicious touchpoints detected by the injection prevention rules are processed according to the set prevention levels.
When the Prevention Level is set to 2 or higher, suspected fraud events are excluded from postbacks. However, you can send them with limitations by completing the Postback settings below.
Sends Target events only: Installs (App), Deeplink Opens (App), and Deeplink Pageviews (App).
Sends events as unattributed.
Sends the identified fraud type.
Postbacks are sent to channels that would have received attribution if not suspected as fraud. These are channels that met all other Airbridge attribution model rules, including touchpoint priority and last-touch attribution (LTA).
Postbacks are sent only to channels with the Postback settings below configured.
In the postback delivery rule, set [Attribution] to All Events
Edit the postback URL as follows. If using the POST method, contact your CSM or reach out through the Airbridge Help Center.
Add a postback parameter. Enter the parameter name specified by the channel and select
{unattributedTouchpointFraudReason}as the parameter value.Some channels require
{unattributedTouchpointClickID}as the Click ID parameter value. Confirm with the channel.
The events attributed to the suspicious touchpoints detected by the set rules can be viewed in your Airbridge reports and raw data export files.
Note
Media Partner cannot access the [App Raw Data Export] menu. The results can only be accessed though the Airbridge reports.
Agency users need to get access permission to the [App Raw Data Export] menu and event properties by the Owner or In-house Marketer. Refer to this article and request access to the Owner or In-house marketer.
1. Navigate to [Raw Data]>[App Raw Data].
2. In the [Request History] tab, click Export raw data.
3. In the [Select Event] step, select the event you want to export. In the [Select Property] step, select Conversion Fraud Tag and Fraud Tags.
4. Export raw data. Events determined to be suspicious by the injection prevention rules are tagged with the Conversion Fraud Tag, Fraud_Touchpoint_FutureTime.
Events that are attributed to the suspicious touchpoints detected by the injection prevention rule can be viewed in the Airbridge reports that support "Touchpoint Fraud Tag" as a GroupBy option.
Supported Airbridge reports: Actuals Report, Trend Report, Retention Report, Revenue Report, Funnel Report with cohort configuration
You can also configure the filter to create a straightforward view.
Touchpoint Fraud TagisFraud_Touchpoint_FutureTime